Verifiable credentials
The commonly used verifiable credential framework, data model, and specification has been defined by the World Wide Web Consortium (W3C) and forms the foundations for Receptor, Redbelly's native identity protocol. It provides a standardised, interoperable way to express and verify claims about individuals, organisations, or things in a tamper-evident and privacy-enhancing manner.
How do verifiable credentials work
There are three key entities with important roles in a verifiable credential data model:
- Issuer - the entity who creates and issues the credential based on information they've verified
- Holder - the entity holding the credential and whose information is contained therein
- Verifier - the entity looking to verify the legitimacy of the credential
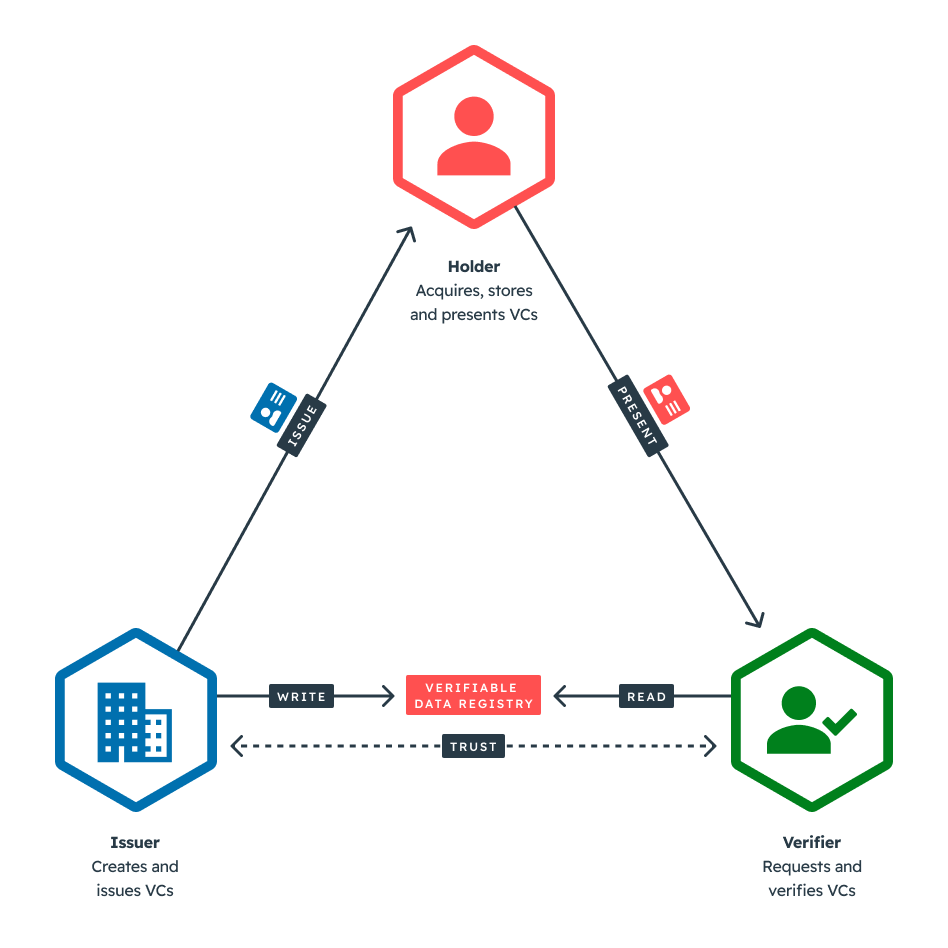
In the verifiable credential data model, the Issuer will create the credential containing the relevant personal information about the Holder, sign it using a cryptographic key, and issue the credential directly to the Holder. The Issuer will also often write some data to a verifiable data registry that can serve as an independent mediator of identifiers, verifiable credential schemas, revocation registries, issuer public keys, etc. Often more than one type of verifiable data registry is used in such a digital identity ecosystem.
Verifiers, such as businesses or smart contracts, can then request Holders to prove some claims about their identity. For example, a business can request proof that the Holder meets specific eligibility criteria for the business’s product or service. The Holder can generate verifiable presentations and share them with the Verifier to make claims - i.e. to prove they possess verifiable credentials within their broader digital identity with specific characteristics.
The Verifier can then use the contents of the verifiable credentials, along with referencing the verifiable data registry (if required), to independently verify the authenticity and integrity of the claim about the Holder’s digital identity.